Highbury_Blade
Bummed in the gob
- Joined
- Aug 9, 2009
- Messages
- 24,619
- Reaction score
- 13,220
I posted about the security of (or lack of security) on SUFC online ticket system on another thread, but's worth highlighing in it's own thread.
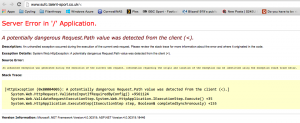
I was trying to replicate a problem that Mousey was having, but i couldn't remember my password. So i followed the instructions to get a new one, expecting that i would get an email with instructions on how to reset my password.
What i actually got was this

They've sent me my actual password, in an email.
What this means, is that your password is stored in a database, unencrypted, and then transmitted in plain over email, which is not a secure medium.
There are a couple of things wrong with this
Firstly your email could get intercepted. They would then have access to your account which means they would have your home address & date of birth. They'd also have access to any details of your friends or family that you have linked to your account. They could then see what your purchase history was. Perhaps you've bought a few tickets for an upcoming away game? Somebody then has your home address, and the knowledge that you're not going to be there on a certain date.
This possible all sounds a bit fanciful, and the likelihood is that that would never happen.
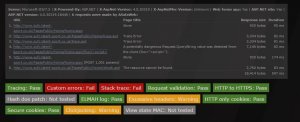
What's for more worrying is that if they're getting password management wrong and storing details unencrypted in a database, what else are they getting wrong? This is a site that takes credit card details. Maybe they're storing them unencrypted too? How vulnerable is the site to all sorts of potential attacks. Password management is the most basic form of ssecurityon a site. If that's been done incorrectly i have very little confidence that they'd be getting much else right.
I was trying to replicate a problem that Mousey was having, but i couldn't remember my password. So i followed the instructions to get a new one, expecting that i would get an email with instructions on how to reset my password.
What i actually got was this

They've sent me my actual password, in an email.
What this means, is that your password is stored in a database, unencrypted, and then transmitted in plain over email, which is not a secure medium.
There are a couple of things wrong with this
Firstly your email could get intercepted. They would then have access to your account which means they would have your home address & date of birth. They'd also have access to any details of your friends or family that you have linked to your account. They could then see what your purchase history was. Perhaps you've bought a few tickets for an upcoming away game? Somebody then has your home address, and the knowledge that you're not going to be there on a certain date.
This possible all sounds a bit fanciful, and the likelihood is that that would never happen.
What's for more worrying is that if they're getting password management wrong and storing details unencrypted in a database, what else are they getting wrong? This is a site that takes credit card details. Maybe they're storing them unencrypted too? How vulnerable is the site to all sorts of potential attacks. Password management is the most basic form of ssecurityon a site. If that's been done incorrectly i have very little confidence that they'd be getting much else right.